Configuring Secure Factory Service
The Secure Factory Command user interface enables you to configure Secure Factory Service and manage Secure Factory CLI workstations.
The Secure Factory Command UI consists of the following configuration screens:
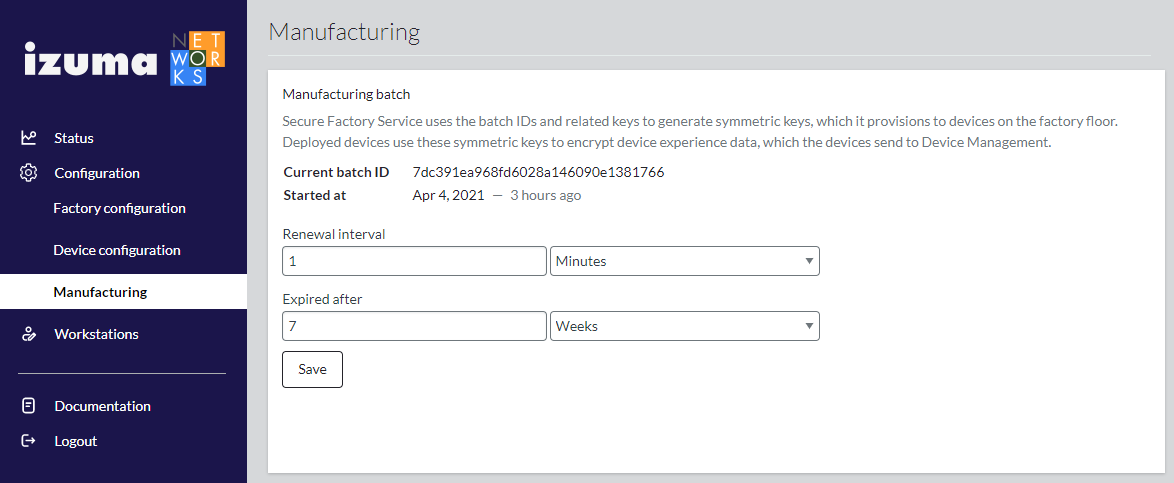
Factory configuration
To set up a factory and generate a factory public key, root of factories CA (optional), CA certificate and LwM2M device certificates:
-
Select Configuration > Factory configuration from the Secure Factory Command side menu.
-
Enter Factory ID and Factory name values.
You provision the factory ID and factory public key to your devices when you integrate your shared key and factory details into your device firmware.
-
Enter Device Management URL and access key values.
You can provide an access key or use Device Management to generate an access key.
-
Switch the Require root of factories toggle on or off. Root of factories is required by default.
If you have multiple factories, signing your factory CAs with a common root of factories CA enables devices that you manufacture in different factories to trust each other.
-
Set the field values in the Certificate authority section of the screen.
Secure Factory Service uses the field values that you enter in the Certificate authority (CA) section of the Factory details screen to set the Issuer and Subject name attributes of the CA certificate that signs LwM2M device certificates.
- Certificate expiration - By default, the certificate is valid for 30 years.
- Organization (optional) - The legal name of the issuing organization. The
Subject: Oattribute of the certificate. - Organizational unit (optional) - The name of the organizational unit issuing the certificate. The
Subject: OUattribute of the certificate. - City (optional) - The city in which the organization is located. The
Subject: Lattribute of the certificate. - State (optional) - The state in which the organization is located. The
Subject: STattribute of the certificate.
Note: We recommend using at most one of these optional fields (also called distinguished name parameters) for the factory CA certificate (for example, Organizational unit) if you have device storage capacity limitations.
-
Click Save.
Warning: When you click Save on the Factory details screen, Secure Factory Service calls the HSM service to generate a factory key pair and certificate, a CA key pair and certificate, and a LwM2M server root CA key pair and certificate, using the information you provide on the screen. After the HSM service generates these credentials, you cannot change them using the Secure Factory Command UI.
-
If the Require root of factories toggle button is on, you must now sign your factory CA certificate with the root of factories CA:
-
Click Download CA CSR.
This downloads a CSR (certificate signing request) PEM file.
-
Sign the CSR with your root of factories CA. You can do this using the root of factories tool.
Important: Be sure to sign your factory CA certificates with the same root of factories CA; this enables devices manufactured in different factories to trust each other.
-
Click Update CA certificate.
This opens the Update factory CA certificate window.
-
Copy and paste your PEM-format certificates into the Factory CA certificate and Root of factories CA certificate fields and click OK.
-
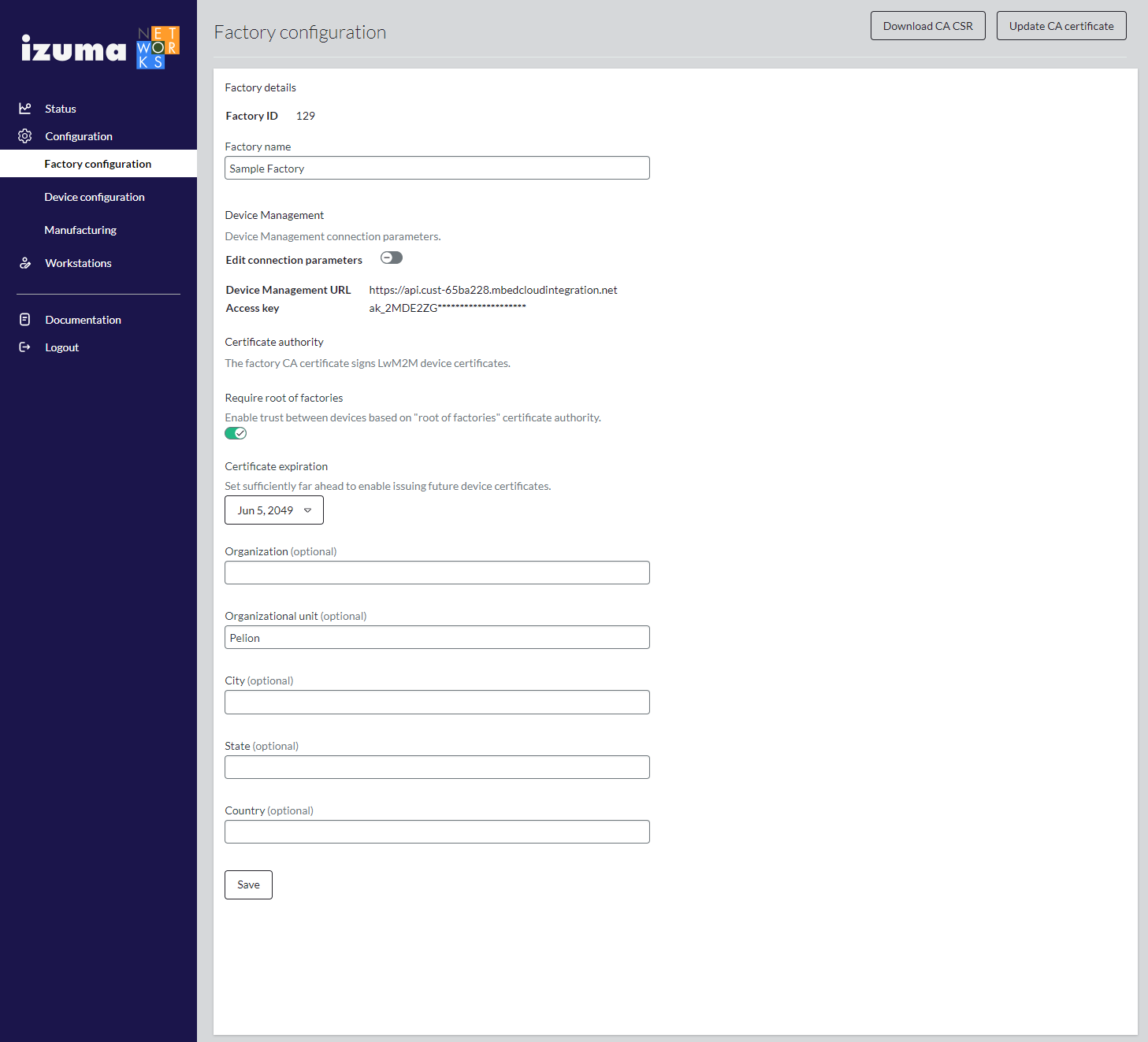
Device configuration
When Secure Factory CLI sends a provisioning request, Secure Factory Service calls the HSM service to generate a unique keypair, which it uses to create a device certificate to provision to the device. The device certificate's Issuer and Subject name attributes are set with the field values that you enter on the Device certificates screen.
To configure the device certificate attributes:
-
Select Configuration > Device configuration from the Secure Factory Command side menu.
-
Set the Organization, Organizational unit, City, and State values, as described in Factory configuration, to define the Subject name attributes of device certificates.
Note: For the device certificate, we recommend not using any of the distinguished name parameters if you have device storage capacity limitations.
-
Define the validity period of generated device certificates in the Valid for fields.
-
Click Save.
Warning: When a device certificate expires, the device can no longer connect to Device Management. You must choose a validity period that is greater than the expected lifetime of the device.
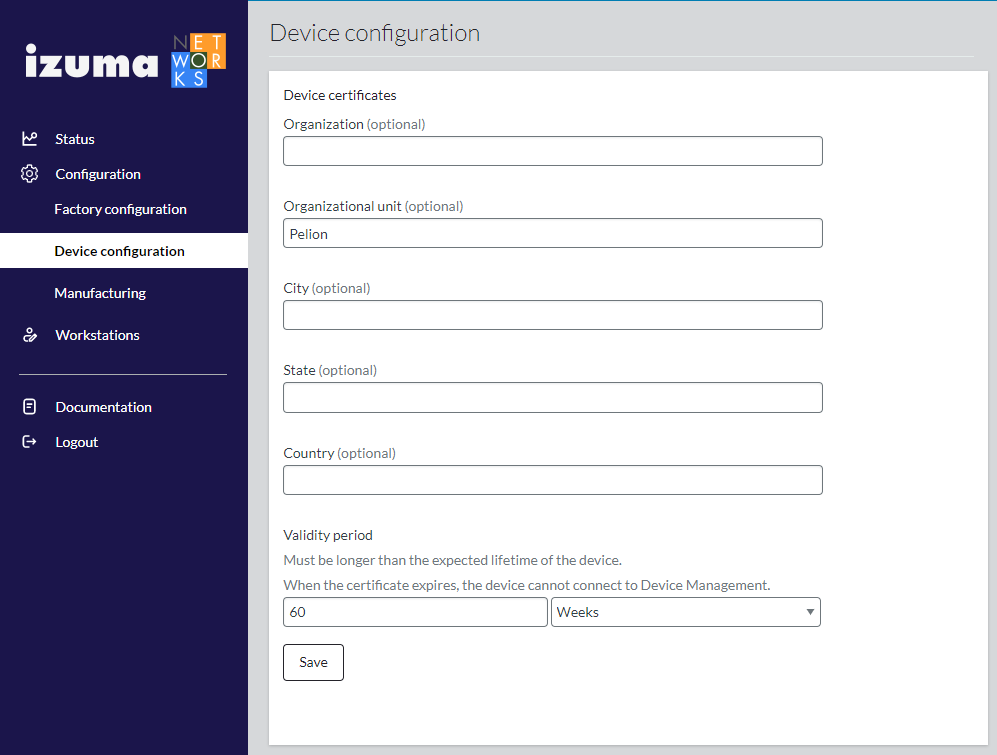
Manufacturing
Secure Factory Service obtains dynamic batch IDs and keys at predefined intervals from Device Management. Secure Factory Service uses these batch IDs and keys to generate symmetric keys, which it provisions to devices on the factory floor. Deployed devices use these symmetric keys to encrypt device experience data, which the devices send to Device Management.
To configure the interval at which Secure Factory Service obtains batch IDs and keys and the period for which the batch IDs and keys are valid:
- Select Manufacturing from the Secure Factory Command side menu.
- Set the Renewal interval and Expired after fields.
Warning: If Secure Factory Service does not obtain a new batch ID and key before the existing ID and key expire, device manufacturing will stop.