Izuma Secure Factory
The Izuma Secure Factory solution enables you to manufacture devices that can connect to Izuma Device Management and ensures the security of your devices, keys and certificates during device provisioning in the factory.
The device provisioning process sets up your devices for secure connection and communication with Izuma Device Management.
Device Management uses security based on Public Key Infrastructure (PKI) and relies on X.509 certificates and public-key encryption for server and device authentication.
Provisioning these credentials to your devices in the factory enables them to trust Device Management and enables Device Management to authenticate your devices when they attempt to connect to your account.
Izuma Secure Factory ensures that:
- Keys, certificates and other provisioned data is secure and not exposed to factory operators.
- Secure data is provisioned only to trusted devices.
Secure Factory architecture
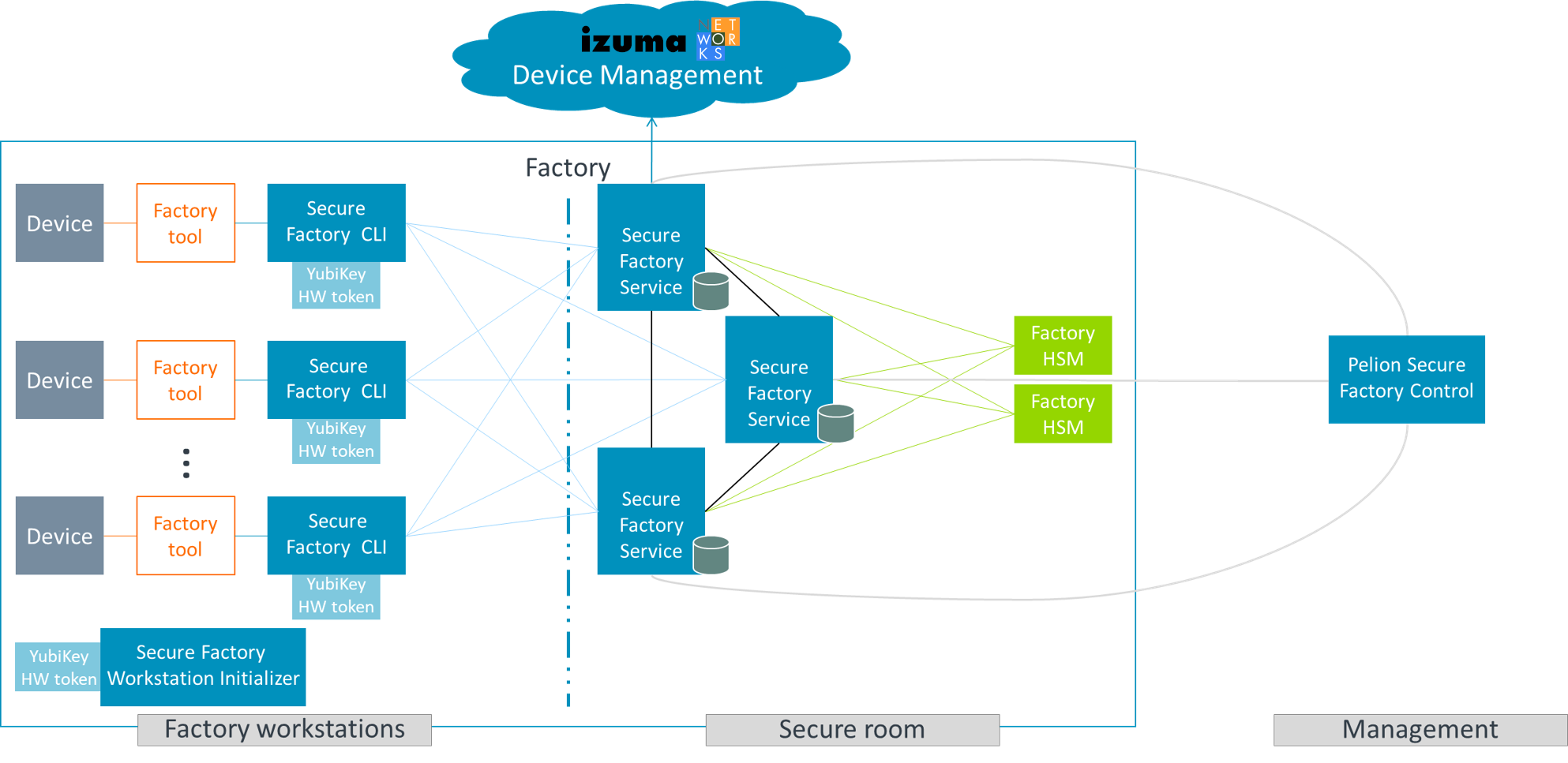
The provisioning process using Izuma Secure Factory involves a secure room, which is isolated from the rest of the factory, and provisioning workstations on the factory floor.
The secure room houses Secure Factory Service servers, which provision credentials and other parameters that devices need to connect to Device Management. It also houses hardware security modules (HSMs), which generate and store keys.
The workstations on the factory floor can provision devices securely using Secure Factory CLI, a command-line interface tool, which integrates into the local factory tool and enables Secure Factory Service to authenticate requests from the factory tool to provision devices.
Secure Factory Service authenticates Secure Factory CLI requests using a unique workstation certificate. To enhance security, the Secure Factory Workstation Initializer generates each workstation's certificate directly on a separate YubiKey hardware token. The workstation operator must insert the token into the workstation, along with a PIN code, before generating requests.
When Secure Factory Service receives an authenticated device provisioning request, it generates a device certificate and signs it using the HSM and then communicates the signed certificate to the device.
All communication from the device, through Secure Factory CLI, to Secure Factory Service is encrypted using the Elliptic-curve Diffie-Hellman (ECDH) protocol. This is made possible by establishing key agreement between the device and Secure Factory Service before the device reaches the provisioning workstation.
This diagram shows the high-level architecture of the Secure Factory solution:
High availability
The Secure Factory Service three-node cluster architecture ensures server failover and high availability of:
- Secure Factory web service and HSM web service.
- Secure Factory Admin service.
- MongoDB database.
Additionally, the two HSMs, on which Secure Factory generates secure credentials, are accessible by all instances of the Secure Factory Service web service.
This ensures that production can continue at the workstations even if one physical machine or HSM becomes unavailable.
Note: Should a second physical machine or HSM go down, Secure Factory will no longer be available until repaired.
Quick links
Installing Secure Factory Service
Installing a Secure Factory CLI workstation
- Install Secure Factory CLI and Secure Factory Workstation Initializer
- Set up Secure Factory CLI workstations
Integrating Secure Factory CLI with your factory tool
Integrate the factory ID and public key into your device firmware
Registering a Secure Factory CLI workstation
Register your workstation using Initializer CLI tool
Approving a Secure Factory CLI workstation registration request
Approve a workstation registration request using Secure Factory Command